1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
| binwalk TL-WDR5620珍珠白\ V6.0_1.0.10\ Build\ 190830\ Rel.56944n.bin
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
43984 0xABD0 U-Boot version string, "U-Boot 1.1.3 (Aug 30 2019 - 10:09:42)"
62464 0xF400 LZMA compressed data, properties: 0x6E, dictionary size: 8388608 bytes, uncompressed size: 3885424 bytes
1287232 0x13A440 LZMA compressed data, properties: 0x5A, dictionary size: 8388608 bytes, uncompressed size: 95491 bytes
1310631 0x13FFA7 LZMA compressed data, properties: 0x5A, dictionary size: 8388608 bytes, uncompressed size: 94952 bytes
1337998 0x146A8E LZMA compressed data, properties: 0x5A, dictionary size: 8388608 bytes, uncompressed size: 94669 bytes
1360409 0x14C219 LZMA compressed data, properties: 0x5A, dictionary size: 8388608 bytes, uncompressed size: 94659 bytes
1380297 0x150FC9 LZMA compressed data, properties: 0x5A, dictionary size: 8388608 bytes, uncompressed size: 94148 bytes
1399946 0x155C8A LZMA compressed data, properties: 0x5A, dictionary size: 8388608 bytes, uncompressed size: 91853 bytes
1420189 0x15AB9D LZMA compressed data, properties: 0x5A, dictionary size: 8388608 bytes, uncompressed size: 89711 bytes
1442119 0x160147 LZMA compressed data, properties: 0x5A, dictionary size: 8388608 bytes, uncompressed size: 85890 bytes
1461740 0x164DEC LZMA compressed data, properties: 0x5A, dictionary size: 8388608 bytes, uncompressed size: 42500 bytes
1472706 0x1678C2 LZMA compressed data, properties: 0x5A, dictionary size: 8388608 bytes, uncompressed size: 7170 bytes
1474229 0x167EB5 LZMA compressed data, properties: 0x5A, dictionary size: 8388608 bytes, uncompressed size: 200 bytes
1474456 0x167F98 LZMA compressed data, properties: 0x5A, dictionary size: 8388608 bytes, uncompressed size: 253 bytes
1474721 0x1680A1 LZMA compressed data, properties: 0x5A, dictionary size: 8388608 bytes, uncompressed size: 14751 bytes
1476674 0x168842 LZMA compressed data, properties: 0x5A, dictionary size: 8388608 bytes, uncompressed size: 493 bytes
1477125 0x168A05 LZMA compressed data, properties: 0x5A, dictionary size: 8388608 bytes, uncompressed size: 2823 bytes
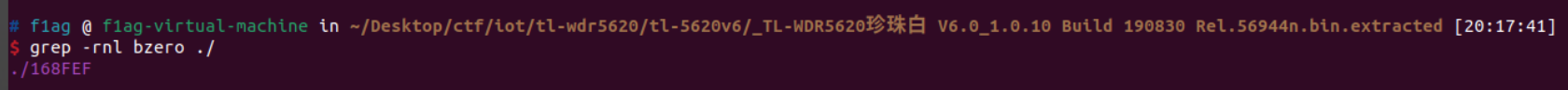
1478639 0x168FEF LZMA compressed data, properties: 0x5A, dictionary size: 8388608 bytes, uncompressed size: 221476 bytes
1550818 0x17A9E2 LZMA compressed data, properties: 0x5A, dictionary size: 8388608 bytes, uncompressed size: 1111 bytes
1551723 0x17AD6B LZMA compressed data, properties: 0x5A, dictionary size: 8388608 bytes, uncompressed size: 1356 bytes
1552122 0x17AEFA LZMA compressed data, properties: 0x5A, dictionary size: 8388608 bytes, uncompressed size: 384 bytes
1552357 0x17AFE5 LZMA compressed data, properties: 0x5A, dictionary size: 8388608 bytes, uncompressed size: 1535 bytes
1552729 0x17B159 LZMA compressed data, properties: 0x5A, dictionary size: 8388608 bytes, uncompressed size: 607 bytes
1553032 0x17B288 LZMA compressed data, properties: 0x5A, dictionary size: 8388608 bytes, uncompressed size: 438 bytes
1553275 0x17B37B LZMA compressed data, properties: 0x5A, dictionary size: 8388608 bytes, uncompressed size: 949 bytes
1553612 0x17B4CC LZMA compressed data, properties: 0x5A, dictionary size: 8388608 bytes, uncompressed size: 566 bytes
1553908 0x17B5F4 LZMA compressed data, properties: 0x5A, dictionary size: 8388608 bytes, uncompressed size: 2536 bytes
1554359 0x17B7B7 LZMA compressed data, properties: 0x5A, dictionary size: 8388608 bytes, uncompressed size: 731 bytes
1554680 0x17B8F8 LZMA compressed data, properties: 0x5A, dictionary size: 8388608 bytes, uncompressed size: 217 bytes
…………
|